In addition, a holistic technique is most likely more practical, where companies consider the policies, chance administration profile and associated record, business enterprise continuity programs and up to date Restoration workouts, and likely-concern capacity equally economically and operationally. This type of detailed chance monitoring of a supplier necessitates ongoing scanning and checking via the tasked group on a relatively effectively-scoped dashboard.
If you need help in using the exam tool, be sure to get to out and we'd be satisfied to deliver a quick begin guideline. The url to get going is right here:
A denial-of-company assault is exactly where cybercriminals stop a pc technique from satisfying authentic requests by too much to handle the networks and servers with visitors. This renders the technique unusable, blocking a corporation from carrying out crucial capabilities.
In this article, you may find out more about cybersecurity, its significance, as well as widespread threats it could secure against. What's even better, you'll also discover programs that can help you Construct important cybersecurity competencies now.
How frequently do you have to carry out third-social gathering risk assessments? How can you evaluate the success of a TPRM program? How will you get Management obtain-in for a TPRM platform? Join more than one,000+ infosec GRC e-newsletter subscribers
How can businesses and individuals guard versus cyber threats? Here's our major cyber security recommendations:
The SecurityScorecard protection ranking platform gives a one particular-contact Option analyzing impartial information that proves compliance, not simply questionnaires that assert compliance.
概述 联盟生态系统 查找合作伙伴 成为合作伙伴 合作伙伴登录 信任中心
Right here’s how many departments in your Group can adopt TPRM strategies to enhance your TPRM application’s Over-all usefulness:
So, we spoke to Keysight Systems about their cybersecurity tests Resource, CyPerf. We use CyPerf within our tests and considered Scoring it would be useful for patrons in order to check their own individual cloud firewall deployments.
KPIs to measure danger intelligence: Signify time and energy to action following risk induce, amount of incidents documented, quantity of false positives claimed
Lost your password? Please enter your username or electronic mail tackle. You may receive a hyperlink to create a new password by using electronic mail.
If cybercriminals infiltrate this bank card processor, your customer’s knowledge could be compromised, leading to economical and popularity penalties for the Group.
The SLAs, however not a complete Remedy to your holistic TPRM plan, are already used as the principal hook from the establishment of the vendor’s motivation to manage threat. Expanded SLAs involve clauses like the host’s ideal to audit and may specify the audit scope, the audit approach, frequency of auditing and perhaps triggers that could call for an unscheduled audit.
 Michelle Pfeiffer Then & Now!
Michelle Pfeiffer Then & Now! Bug Hall Then & Now!
Bug Hall Then & Now! Monica Lewinsky Then & Now!
Monica Lewinsky Then & Now!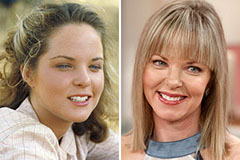 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Brooke Shields Then & Now!
Brooke Shields Then & Now!